Security and Prevention against Phishing and Spam email
By Phoenix Information Technology Services – Julio Cardenas
Email spam, also known as junk email or unsolicited bulk email (UBE), is a subset of electronic spam involving nearly identical messages sent to numerous recipients by email. Clicking on links in spam email may send users to phishing web sites or sites that are hosting malware.
Phishing is the act of attempting to acquire information such as usernames, passwords, and credit card details
(and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.
SPAM:
Statistics and Estimates
The total volume of email spam has been consistently growing, but in 2011 the trend seems to have reversed. The amount of spam users see in their mailboxes is only a portion of total spam sent, since spammers’ lists often contain a large percentage of invalid addresses and many spam filters simply delete or reject “obvious spam.”
The first known spam email, advertising a DEC product presentation, was sent in 1978 by Gary Thuerk to 600 addresses, which was all the users of ARPANET at the time, though software limitations meant only slightly more than half of the
intended recipients actually received it. As of August 2010, the amount of spam was estimated to be around 200 billion spam messages sent per day. More than 97% of all emails sent over the net are unwanted, according to a Microsoft security report. The Messaging Anti-Abuse Working Group (MAAWG) estimates that 85% of incoming mail is “abusive email”, as of the second half of 2007. The sample size for the MAAWG’s study was over 100 million mailboxes.
A 2010 survey of US and European email users showed that 46% of the respondents had opened spam messages, although only 11% had clicked on a link.
Cost of spam
A 2004 survey estimated that lost productivity costsInternet users in the United States $21.58 billion annually, while
another reported the cost at $17 billion, up from $11 billion in 2003. In 2004, the worldwide productivity cost of spam has been estimated to be $50 billion in 2005. An estimate of the percentage cost borne by the sender of marketing junk mail (snail mail) is 88%, whereas in 2001 one spam was estimated to cost $0.10 for the receiver and $0.00001 (0.01% of the cost) for the sender.
SHOCKING!
In the United States, most states enacted anti-spam laws during the late 1990s and early 2000s. Many of these have since been pre-empted by the less restrictive CAN-SPAM Act of 2003. Spam is legally permissible according to the CAN-SPAM Act of 2003 provided it follows certain criteria: a “truthful” subject line, no forged information in the technical headers or sender address, and other minor requirements. If the spam fails to comply with any of these requirements it is illegal. Aggravated or accelerated penalties apply if the spammer harvested the email addresses using methods described earlier.
A review of the effectiveness of CAN-SPAM in 2005 by the Federal Trade Commission (the agency charged with CAN-SPAM enforcement) stated that the amount of sexually explicit spam had significantly decreased since 2003 and the total volume had begun to level off. Senator Conrad Burns, a principal sponsor, noted that “Enforcement is key regarding the CANSPAM
legislation.” In 2004, less than 1% of spam complied with the CANSPAM Act of 2003. In contrast to the FTC evaluation, many observers view the CAN-SPAM act as having failed in its purpose of reducing spam.
PHISHING
The Beginning
A phishing technique was described in detail in 1987, and (according to its creator) the first recorded use of the term “phishing” was made in 1995. The term is a variant of fishing, probably influenced by phreaking, and alludes to “baits” used in hopes that the potential victim will “bite” by clicking a malicious link or opening a malicious attachment, in which case their financial information and passwords may then be stolen.
Spear Phishing
Phishing attempts directed at specific individuals or companies have been termed spearphishing. Attackers may gather personal information about their target to increase their probability of success.
Clone Phishing
A type of phishing attack whereby a legitimate, and previously delivered, email containing an attachment or link has had its content and recipient address(es) taken and used to create an almost identical or cloned email. The attachment or Link within the email is replaced with a malicious version and then sent from an email address spoofed to appear to come from the original sender. It may claim to be a re-send of the original or an updated version to the original.
Whaling
Several recent phishing attacks have been directed specifically at senior executives and other high profile targets within businesses, and the term whaling has been coined for these kinds of attacks.
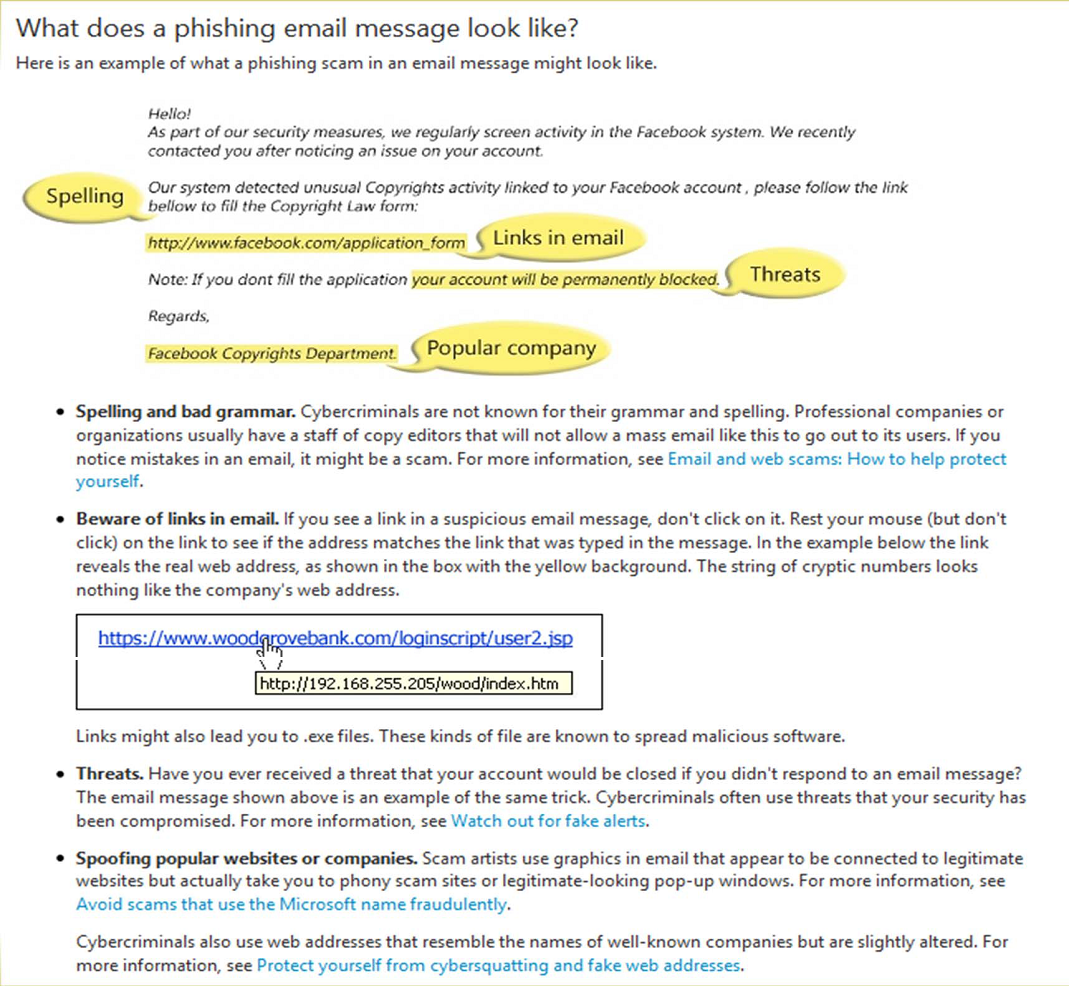
Link manipulation
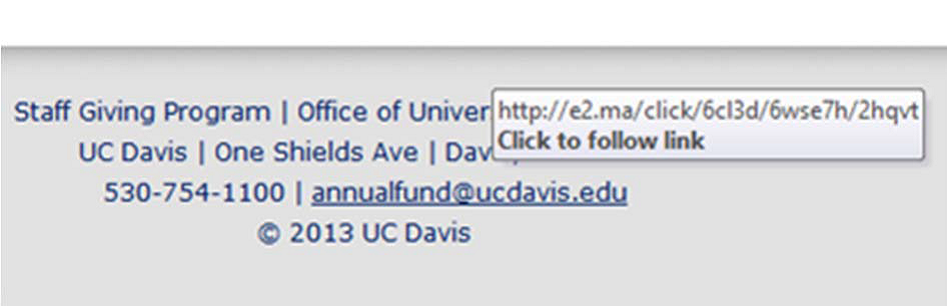
Most methods of phishing use some form of technical deception designed to make a link in an e-mail (and the spoofed website it leads to) appear to belong to the spoofed organization. Misspelled URLs or the use of subdomains are common tricks used by phishers. In the following example URL, http://www.yourbank.example.com/, it appears as though the URL will take you to the example section of the yourbank website; actually this URL points to the “yourbank” (i.e. phishing) section of the example website. Another common trick is to make the displayed text for a link (the text between the <A> tags) suggest a reliable destination, when the link actually goes to the phishers’ site. The following example link, //en.wikipedia.org/wiki/Genuine, appears to direct the user to an article entitled “Genuine”; clicking on it will in fact take the user to the article entitled “Deception”. Hovering your cursor over the link for a couple of seconds may do a similar thing, but this can still be set by the phisher.
Website forgery
Once a victim visits the phishing website, the deception is not over. Some phishing scams use JavaScript commands in order to alter the address bar. This is done either by placing a picture of a legitimate URL over the address bar, or by closing the original address bar and opening a new one with the legitimate URL.
Phone phishing
Not all phishing attacks require a fake website. Messages that claimed to be from a bank told users to dial a phone number regarding problems with their bank accounts.Once the phone number (owned by the phisher, and provided by a Voice over IP service) was dialed, prompts told users to enter their account numbers and PIN. Vishing (voice phishing) sometimes uses fake caller-ID data to give the appearance that calls come from a trusted organization.
Eliminating Phishing and Spam Emails
1) Specialized spam filters can reduce the number of phishing e-mails that reach their addressees’ inboxes. These approaches rely on machine learning and natural language processing approaches to classify phishing e-mails.Email address authentication is another new approach.
2) Guard against spam. Be especially cautious of emails that:
* Come from unrecognized senders.
* Ask you to confirm personal or financial information over the Internet and/or make urgent requests for this information.
* Aren’t personalized.
* Try to upset you into acting quickly by threatening you with frighteninginformation
3) Communicate personal information only via phone or secure web sites. In fact:
When conducting online transactions, look for a sign that the site is secure such as a lock icon on the browser’s status bar or a “https:” URL whereby the “s” stands for “secure” rather than a “http:”.
Also, beware of phone phishing schemes. Do not divulge personal information over the phone unless you initiate the call. Be cautious of emails that ask you to call a phone number to update your account information as well.
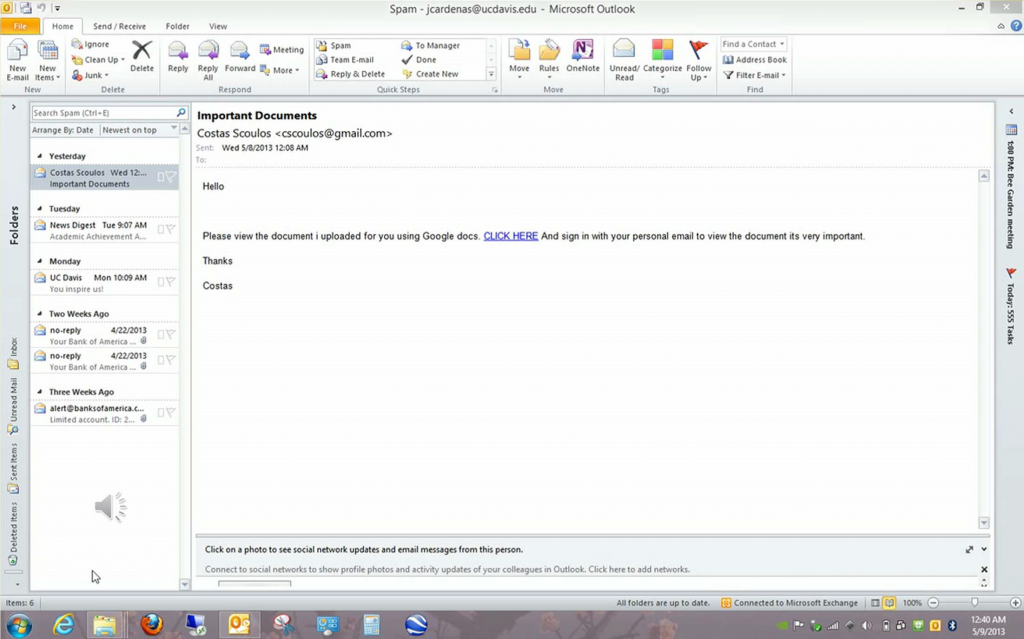
4) Do not click on links, download files or open attachments in emails from unknown senders. It is best to open attachments only when you are expecting them and know what they contain, even if you know the sender.
5) Never email personal or financial information, even if you are close with the recipient. You never know who may gain access to your email account, or to the person’s account to whom you are emailing.
6) Beware of links in emails that ask for personal information, even if the email appears to come from an enterprise you do business with. Phishing web sites often copy the entire look of a legitimate web site, making it appear authentic. To be safe,
call the legitimate enterprise first to see if they really sent that email to you. After all, businesses should not request personal information to be sent via email.
7) Beware of pop-ups and follow these tips:
* Never enter personal information in a pop-up screen.
* Do not click on links in a pop-up screen.
* Do not copy web addresses into your browser from pop-ups.
* Legitimate enterprises should never ask you to submit personal information in popup
screens, so don’t do it.
8) Protect your computer with a firewall, spam filters, anti-virus and antispyware software. Do some research to ensure you are getting the most up-todate software, and update them all regularly to ensure that you are blocking from new viruses and spyware.
9) Check your online accounts and bank statements regularly to ensure that no unauthorized transactions have been made.